With Web SCADA, Digital Oilfield, and the Internet of Things starting to make greater inroads, it is important to step back and understand that with all of the convenience of remote monitoring comes a risk of malicious “hacking” that opens your data — and operations of your Internet-connected SCADA — to criminals from around the world.
With the WannaCry ransomware attack that hit small to medium sized companies in the industry that caused many businesses to halt their daily operations to deal with the aftermath of the attack, WannaCry is a reminder that extra precautions are necessary to keep your industrial operations safe and secure.
We will focus on industrial monitoring (such as tank-level, EFMs, or Heat-Stress) as opposed to consumables (like home security cameras) and what steps need to be in place to prevent unwanted and malicious users from access your SCADA devices. In this particular article we will go over the steps needed to secure IP-based cell data connection as it is the most popular form of remote access to the field.
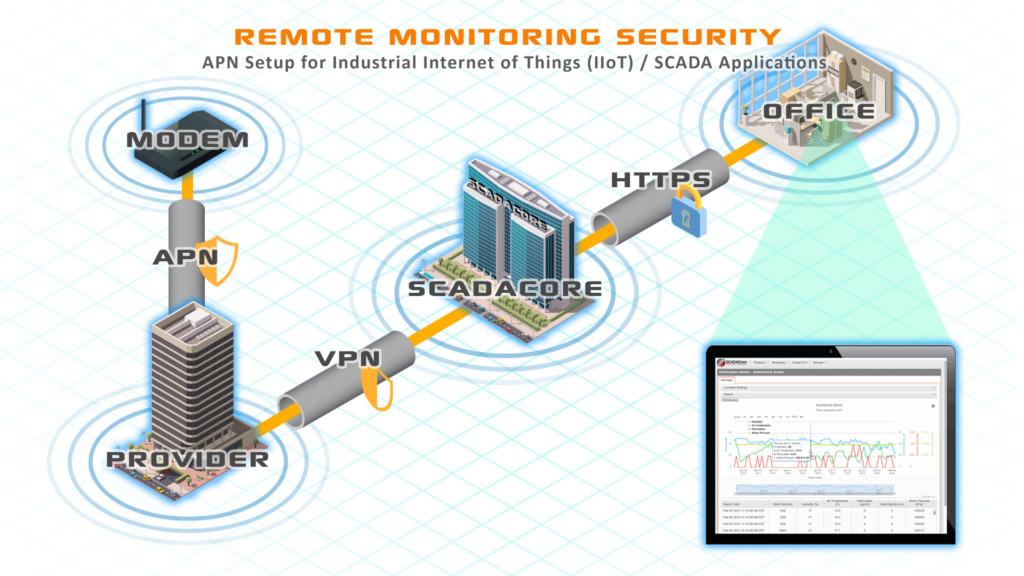
1. APNs – Securing your modems behind a private Network
The best way to protect your device from malicious remote access is to keep your device off the public Internet. Far too often, Internet providers or SCADA Integrators will opt for the easy solution — which is a Public IP that is accessible from anywhere in the world. SCADACore always highly recommends against Public IPs, as it opens a door to your devices. Public IPs are doors that can be locked, but it is still a door that can be used. At the very least, the remote malicious users will attempt to login to your devices or modem and drive up your usage fees.
APN – Access Point Names are set up by your cell provider to only allow servers, connected via VPN to the provider, to access the modems. It is similar to a LAN that you have in your home. The APN is set in your modem . This will provide your device with an IP address that is not accessible from the outside world, and it is ONLY accessible from your server.
This has its drawbacks, however, as only one server has access to the data. If multiple users want access to the data, they will also have to pay a fee and set up a VPN with the service provider. SCADACore provides an additional option with Connect Live M2M that allows authenticated users to connect to the SCADACore Live webpage via HTTPS authentication. Then connect via secondary authentication to an individually secured server inside the APN and access the device through the SCADACore Live webpage.
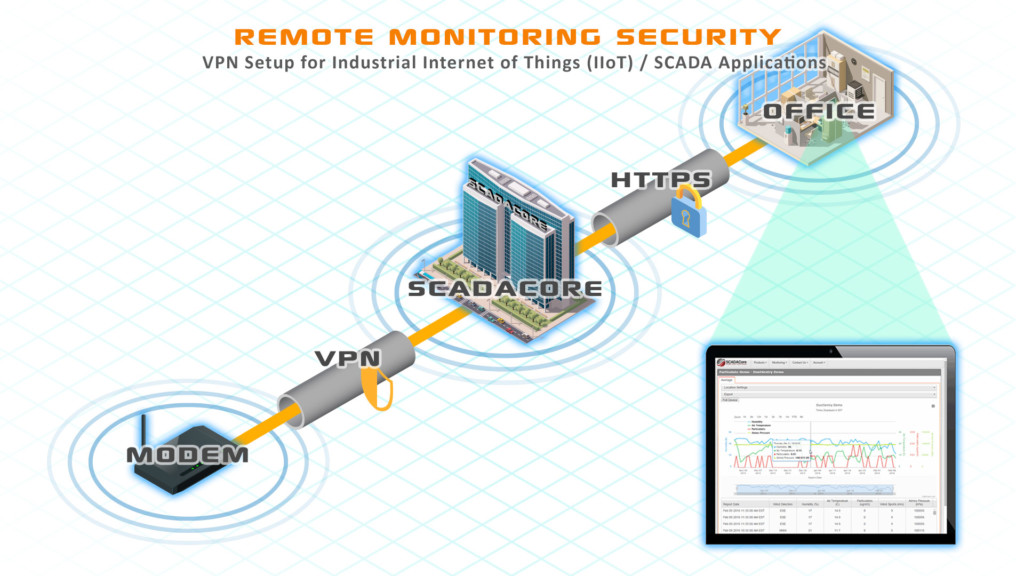
2. VPNs
VPNs, or Virtual Private Networks, are a good solution when multiple entities need to access the same remote device. Most cellular modems will have basic VPN configuration and access so this is a viable option for most cell modems.
It is, however, a little difficult to set up and requires software on both ends to bridge the connection. The additional need to start your VPN software on your computer or mobile device is the most common reason for ignoring the VPN setup, but if the alternative to the VPN is an public open Internet device, then the extra trouble to set up the VPN is worthwhile.
Since the VPN requires a “handshake” before it is accessible, the modem will not be accessed from the outside, meaning the usage is still under control with no surprise-thousand-dollar-bill at the end of the month.
3. Use uncommon ports
Whenever possible, avoid using the 80 port it is the most common HTTP port and will be the first port that is attempted by malicious users. All modems will allow users to configure services from ports 1 – 65535. Commonly used ports to avoid are:
- 21-FTP
- 22-SSH/SFTP
- 23-Telnet
- 25-SMTP
- 53-DNS
- 80-HTTP
- 443-HTTPS
4. Lock down unwanted ports
Many of the modems have open ports that come pre-configured by default. These ports include services such as FTP, SSH, Telnet, SMTP, and DNS that are very rarely used for SCADA applications. Simply logging into the modem and turning off these services will prevent outside users from finding your open device.
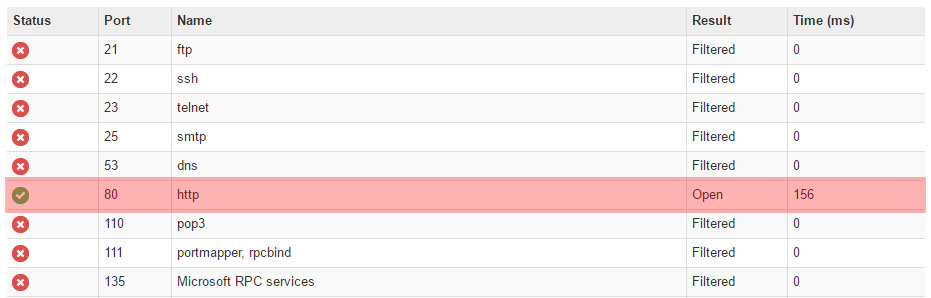
Example of a Modem with Open Ports
There are millions of devices online, hackers will try the most common exploits and services first and may move along rather than scanning the additional 65000 ports.
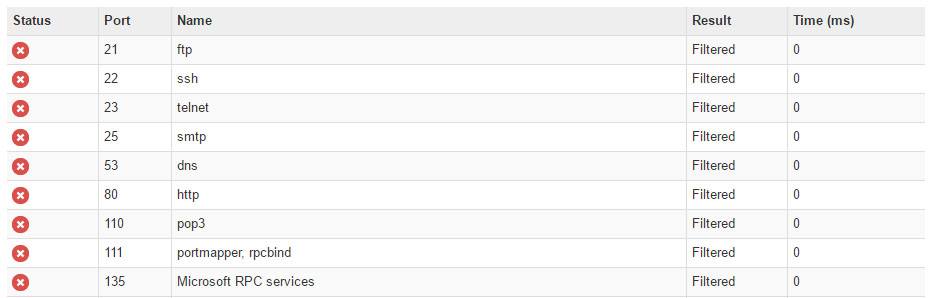
Example of Modem with Secured Ports
In addition, if the ports are not closed, you will have “attempts” against you. One FTP attempt could use 1 kilobyte of data from your plan. If you had 5 attempts each minute to access your device by the end of the month your usage could be as high as 216,000KB on one port with one service. These usage attempts can end up costing thousands in data fees by the end of the year.
MxToolBox provides a useful tool to scan your Modem or any IP Address to find any open ports.
5. Enable security on end devices, if available
If possible, the passwords to login to end devices can be changed for an added layer of security. This is done to prevent access to the end devices by unauthorized users who know the default passwords for the brand and model of the device.
6. Monitor usage and create black-lists when you can
Many providers will now provide real-time or near-real-time updates on the modem usage. Unexpected high usage on a public modem is always a sign that the modem is being used maliciously from the unknown actor.
7. Change the default password
This should go without saying, it takes less than 5 minutes to change a login from its default admin/admin.
SCADACore conducted a survey of 255 sites that were used by a common Internet provider for Public IP modems in the field. We found that of the 255 sites, 10 of them still had their default password associated with it.
With a default password to the admin tools, a malicious user would have full control of your system. They could shut down your modem, access your devices, use your modem as a proxy or spam-bot and drive up usage. Recently, using your modem to purchase products or apps using SMS is happening much more often.
One particular SCADACore client (before moving to SCADACore) had $80,000 in charges on a single modem. After an investigation by the telecom company, the charges were, of course, found to be fraudulent and waived; but a less understanding provider may not have been so quick to waive the fees.
SCADACore Advantage
SCADACore has provided many clients with complete, one-stop communication packages. SCADACore takes care of all the billing and configuration details, and provide our clients with a simple, all-inclusive solution at an affordable price. Click the button below to see how we can help!